Blog
IT EXPERTISe
OUR BLOG.

By Alan Kluba
•
08 Feb, 2024
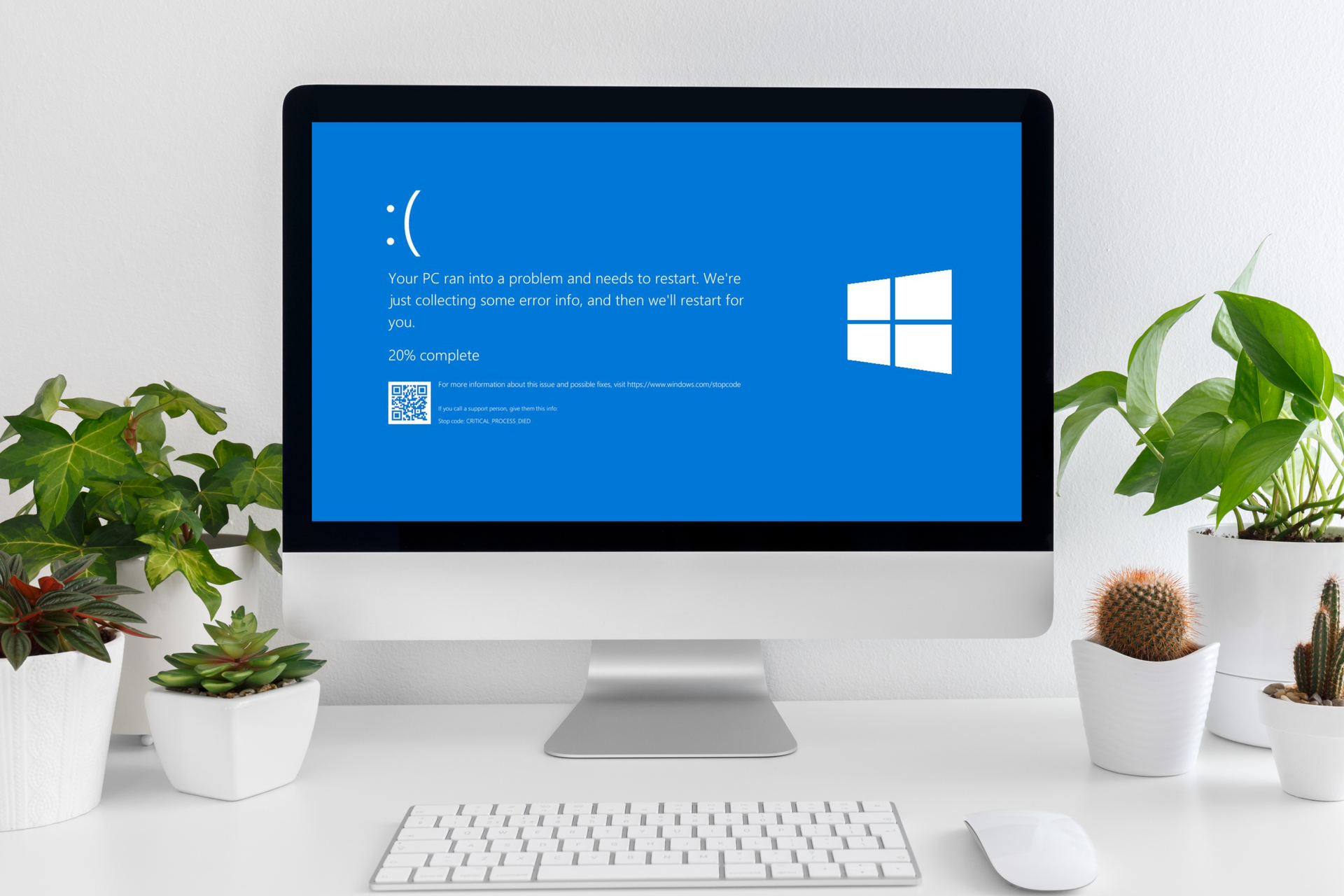
The healthcare industry remains one of the prime targets for external and internal cyber attacks, as protected health information (PHI) is in high demand on the dark web. The frequency and sophistication of attacks continue to rise, posing significant challenges to the healthcare sector. Malware Attacks by Industry - Sonicwall CyberThreat report 2023 Education Healthcare Finance Retail Government Key Challenges facing healthcare Keeping critical infrastructure covered and continuously available Protecting patient privacy from insider risks Preserving the integrity of healthcare data Preventing data breaches originating from ransomware and phishing attacks HSE Attack This attack highlighted the devastating impact of cyber attacks on healthcare infrastructure in Ireland disrupting operations and compromised patient data. MARCH 2021: An email was sent on the 16th of March, opened on the 18th of March 2021 which delivered the lethal blow. MARCH 2021: The HSE antivirus software detected malicious activity on 31st March 2021, monitor only mode. MAY 2021: Mid May HSE operations were finally alerted to the attack by a service provider. JUNE 2021: At least three quarters of the HSE's IT servers had been decrypted and 70% of PC’s were back in use. SEPTEMBER 2021: 90% of systems were recovered. Impact of an Attack The consequences of such attacks extend far beyond financial losses, affecting patient care and safety. Patients don’t get the care they need when healthcare providers are taken offline due to ransomware attacks. Surgeons postpone surgeries because the information necessary to perform a life-saving surgery becomes inaccessible. Failures in diagnostic procedures and laboratory tests result in delayed medical treatment. Emergency Room (ER) bypass causes ambulances to diverge to healthcare facilities miles farther, leading to degraded and irreversible outcomes. What can you do to protect your healthcare organisation from similar attacks: Implementing a multi-layer protection platform can help mitigate vulnerabilities and defend against evolving cyber threats. Healthcare organisations must invest in robust security measures to safeguard critical infrastructure, protect patient privacy, and prevent data breaches. Infinity IT and SonicWall have worked with healthcare providers to help build a healthier system. Our innovations and comprehensive strategies have allowed us to meet new expectations regarding improving security, increasing operation efficiencies, and reducing IT costs. Our knowledge and wealth of experience helps us to help Healthcare Organisation’s to avoid surprises and spend more time focused on their primary mission: ensuring the health and well-being of the communities they serve. As threats continue to evolve, the healthcare industry must remain vigilant and proactive in addressing cybersecurity risks. By learning from past attacks and investing in effective security measures, healthcare organisations can better protect their systems, safeguard patient data, and uphold the trust and integrity of the healthcare system. The time to act is now – the health and well-being of patients depend on it. Case Study: “Our improved security performance coupled with simplified security management has reduced costs and time spent on administrative tasks. The whole process has been a very positive experience!” Steve Jackson IT Director Kingdom Services Group

By Alan Kluba
•
01 Feb, 2024
Recent data breaches across healthcare organisations highlight the urgency for robust cybersecurity measures. In this blog post, we explore the challenges faced by the healthcare industry and how Infinity IT's comprehensive cybersecurity solutions are helping organisations protect their digital infrastructure. The Alarming Rise of Healthcare Cyberattacks: Hacking incidents, particularly targeting network servers and emails, account for over 80% of attacks, posing significant threats to electronic health records (EHR) and personal health records (PHR). Understanding the Impact: The implications of healthcare data breaches extend beyond compromised records. Cyberattacks can lead to severe consequences, affecting the efficiency of medical procedures, increasing mortality rates, and causing long-term financial and mental distress for patients. The evolving tactics of cybercriminals demand a proactive and resilient cybersecurity approach to ensure the safety of patient care. Infinity IT and SonicWall have joined forces to address this challenge. For the past three decades, SonicWall has been at the forefront of cybersecurity, working closely with healthcare providers to enhance security, and operational efficiency, and reduce IT costs. Our Boundless Cybersecurity approach integrates security, central management, advanced analytics, and unified threat management across their entire security solutions portfolio, forming the robust Capture Cloud Platform. Essential Cybersecurity Solutions for Healthcare Organisations: In the face of advancing threats and government-backed ransomware assaults, our cybersecurity solutions emerge as a vital lifeline. These solutions strengthen networks, secure IoT medical devices, and safeguard patient data. Our portfolio comprehensively addresses the intricate security requirements of the healthcare sector, providing a crucial defense against cyber threats. To Summarise: Healthcare organisations must prioritise cybersecurity to ensure patient safety and the uninterrupted delivery of care. Our Cybersecurity approach and comprehensive solutions offer a strategic advantage, empowering healthcare providers to proactively defend against evolving threats and secure the future of healthcare delivery. As the healthcare industry navigates the challenges of an increasingly digital landscape, SonicWall stands as a trusted partner, dedicated to closing the cybersecurity gap for enterprises, governments, and SMBs worldwide. Case Study: “The SMA device rapidly allowed our newly deployed workforce complete access to their internal applications. We now have physicians working from home without problem. We extended our physicians reading environment to their homes, and we’ve moved our scheduling department from in-house to at-home workers.” Michael Brown, IT Director, Women’s Center for Radiology

By Shane Casey
•
16 Nov, 2023
Enhancing Password Security and Authentication Practices Authentication, as defined by the National Institute of Standards and Technology (NIST, 2023), is the process of verifying the identity of a user, process, or device, typically required before granting access to information system resources. Traditionally, this has been accomplished through one-factor authentication—something you know, such as a password or PIN. However, the evolving threat landscape has led to the adoption of multifactor authentication, which combines two or more authentication factors, enhancing security significantly. Multifactor Authentication: Strengthening Identity Verification Multifactor authentication typically involves combining something you know (like a password) with something you have (like a mobile token or key) or something you are (such as facial recognition or fingerprints). For instance, a common multifactor approach is combining a password (something you know) with a one-time PIN sent to your mobile phone (something you have). While multifactor authentication provides heightened security, it's essential to understand that it may impact system availability. Password Policy: A Critical Element Password policy plays a vital role in access administration. It sets the rules for password parameters, including length, complexity, age, and reuse. Recent Microsoft research highlights the importance of well-designed password policies, as overly frequent password changes can lead to predictability, with users selecting easily guessable passwords. Effective password policies and user training are essential to ensure that users grasp the responsibility they bear for safeguarding their passwords. Learning from Real-World Incidents Recent headlines, such as the Colonial Pipeline attack by the Darkside hacker group, underscore the significance of password and security policies. In this case, an employee's use of their company username and password on a compromised external site led to the breach, emphasising the need for robust security controls like two-factor authentication (2FA). This incident serves as a stark reminder of the potential consequences of lax password practices. The Role of Encryption Beyond password security, the way passwords and sensitive data are stored is crucial. Storing passwords in plain text or without encryption poses significant confidentiality and integrity risks if compromised. Encryption, the process of converting human-readable text into incomprehensible ciphertext, plays a pivotal role in modern IT systems. Various encryption techniques, including Secure Socket Layer (SSL) for web traffic and Advanced Encryption Standard (AES) for files, serve different purposes, utilising symmetric or asymmetric encryption methods as needed. Harnessing the Power of Hashing Hashing, though distinct from encryption due to the absence of a key and its non-reversible nature, is a valuable tool for document verification, digital signatures, and ensuring data integrity (NIST, 2022). Hash functions calculate a unique output, known as a hash digest, for input data of any size, making it a fundamental component of modern security practices. In conclusion, adopting multifactor authentication, implementing robust password policies, learning from real-world security incidents, and ensuring data encryption and hashing are fundamental steps toward enhancing your organisation's security posture in an ever-evolving digital landscape. Stay vigilant and informed to protect your digital assets effectively. Author: Shane Casey

By Alan Kluba
•
04 Oct, 2023
DPI SSL is a technology used to inspect and secure encrypted internet traffic. DPI SSL traffic is intercepted by the firewall and decrypted. Once the traffic is decrypted, the firewall can apply various security and content filtering policies to the traffic, including Content Filtering, Intrusion Prevention, Antivirus Scanning and Application Control. Neglecting DPI SSL can leave your network vulnerable to hidden dangers, compliance violations, and productivity issues.

By Shane Casey
•
30 Aug, 2023
This Threat Landscape post underscores the importance of a proactive approach to security, emphasizing the need for asset understanding, threat awareness, and effective controls in today's ever-evolving security landscape. Stay informed and take action to protect your organization from emerging threats and vulnerabilities.
GET IN TOUCH
WITH US
Call Infinity IT today to see how we can help you put a cost effective solution in place for your business.
Email: solutions@infinityit.ie
Dublin (Head Office)
Infinity IT Ltd, 17 The Mall,
Beacon Court, Sandyford,
Dublin 18.
Tel : 01 - 293 0090
Fax : 01 - 293 0137
Cork (Branch Office)
Infinity IT Ltd, Merchant House, Tivoli Industrial Estate, Tivoli, Cork.
Tel : 021 - 7011600
Fax : 01 - 293 0137
Contact Us
Thank you for contacting us.
We will get back to you as soon as possible.
We will get back to you as soon as possible.
Oops, there was an error sending your message.
Please try again later.
Please try again later.